Task 1: Room Outline
This room will cover the concepts of Threat Intelligence and various open-source tools that are useful. The learning objectives include:
- Understanding the basics of threat intelligence & its classifications.
- Using UrlScan.io to scan for malicious URLs.
- Using Abuse.ch to track malware and botnet indicators.
- Investigate phishing emails using PhishTool
- Using Cisco’s Talos Intelligence platform for intel gathering.
Task 2: Threat Intelligence
Threat Intelligence is the analysis of data and information using tools and techniques to generate meaningful patterns on how to mitigate against potential risks associated with existing or emerging threats targeting organisations, industries, sectors or governments.
To mitigate against risks, we can start by trying to answer a few simple questions:
- Who’s attacking you?
- What’s their motivatio-
What a dang minute… These info are the same as the previous room >:V
Go there if you wanna read more about it!! 2.1. Intro to Cyber Threat Intel
Task 3: UrlScan.io
Urlscan.io is a free service developed to assist in scanning and analysing websites. It is used to automate the process of browsing and crawling through websites to record activities and interactions.
When a URL is submitted, the information recorded includes the domains and IP addresses contacted, resources requested from the domains, a snapshot of the web page, technologies utilised and other metadata about the website.
Scan Results: URL scan results provide ample information, with the following key areas being essential to look at:
- Summary: Provides general information about the URL, ranging from the identified IP address, domain registration details, page history and a screenshot of the site.
- HTTP: Provides information on the HTTP connections made by the scanner to the site, with details about the data fetched and the file types received.
- Redirects: Shows information on any identified HTTP and client-side redirects on the site.
- Links: Shows all the identified links outgoing from the site’s homepage.
- Behaviour: Provides details of the variables and cookies found on the site. These may be useful in identifying the frameworks used in developing the site.
- Indicators: Lists all IPs, domains and hashes associated with the site. These indicators do not imply malicious activity related to the site.
Questions
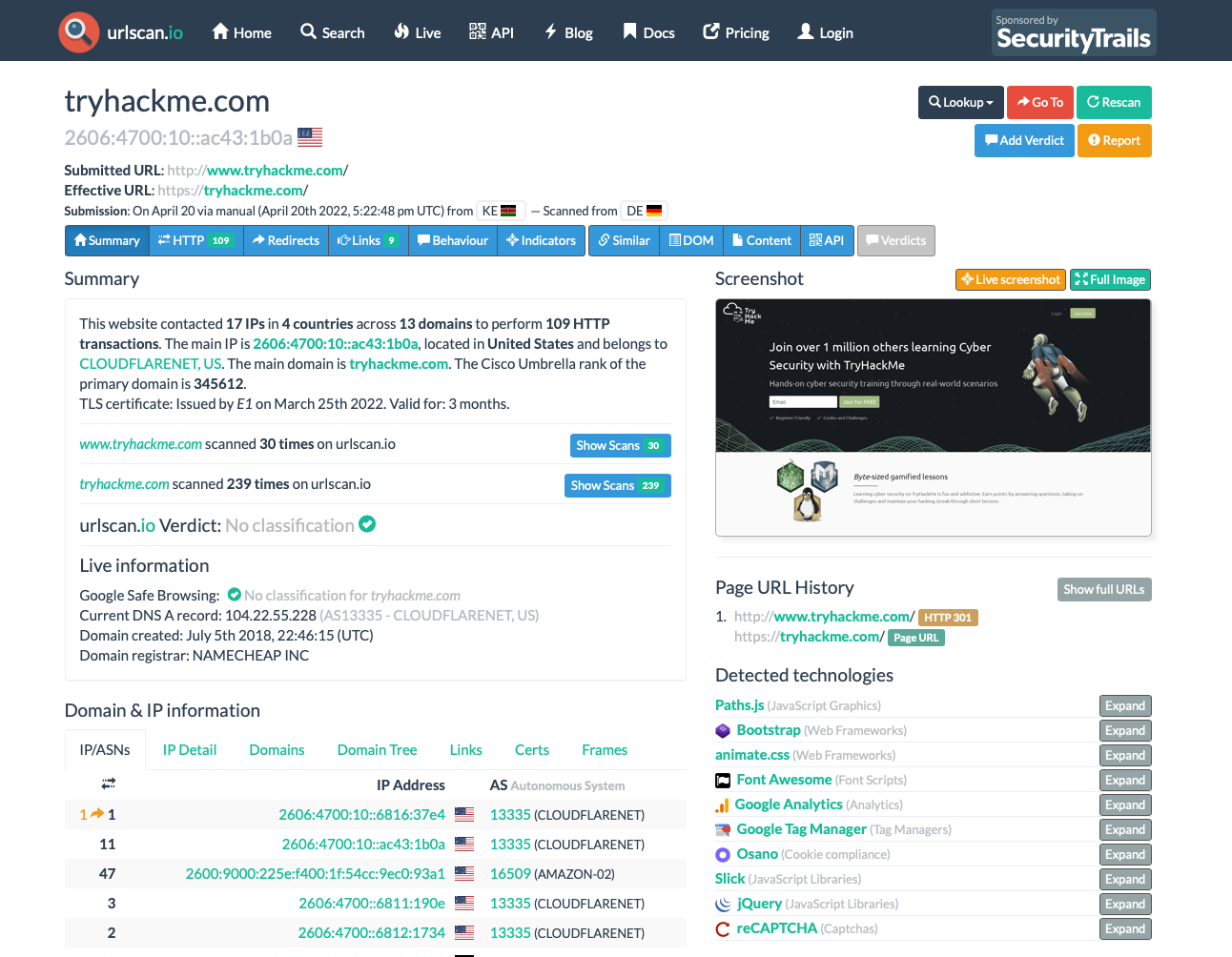
You have been tasked to perform a scan on TryHackMe’s domain. The results obtained are displayed in the image below. Use the details on the image to answer the questions:
What was TryHackMe’s Cisco Umbrella Rank based on the screenshot?
Answer
345612
How many domains did UrlScan.io identify on the screenshot?
Answer
13
What was the main domain registrar listed on the screenshot?
Answer
namecheap inc
What was the main IP address identified for TryHackMe on the screenshot?
Answer
2606:4700:10::ac43:1b0a
Task 4: Abuse.ch
Abuse.ch is a research project hosted by the Institue for Cybersecurity and Engineering at the Bern University of Applied Sciences in Switzerland. It was developed to identify and track malware and botnets through several operational platforms developed under the project.
These platforms are:
- Malware Bazaar: As the name suggests, this project is an all in one malware collection and analysis database. The project supports the following features:
-
- Malware Samples Upload: Security analysts can upload their malware samples for analysis and build the intelligence database. This can be done through the browser or an API.
- Malware Hunting: Hunting for malware samples is possible through setting up alerts to match various elements such as tags, signatures, YARA rules, ClamAV signatures and vendor detection.
-
- Feodo Tracker: With this project, Abuse.ch is targeting to share intelligence on botnet Command & Control (C&C) servers associated with Dridex, Emotes (aka Heodo), TrickBot, QakBot and BazarLoader/BazarBackdoor.
- This is achieved by providing a database of the C&C servers that security analysts can search through and investigate any suspicious IP addresses they have come across.
- Additionally, they provide various IP and IOC blocklists and mitigation information to be used to prevent botnet infections.
- SSL Blacklist: Abuse.ch developed this tool to identify and detect malicious SSL connections. From these connections, SSL certificates used by botnet C2 servers would be identified and updated on a denylist that is provided for use.
- The denylist is also used to identify JA3 fingerprints that would help detect and block malware botnet C2 communications on the TCP layer.
- You can browse through the SSL certificates and JA3 fingerprints lists or download them to add to your deny list or threat hunting rulesets.
- URL Haus: As the name points out, this tool focuses on sharing malicious URLs used for malware distribution. As an analyst, you can search through the database for domains, URLs, hashes and filetypes that are suspected to be malicious and validate your investigations.
- Threat Fox: With ThreatFox, security analysts can search for, share and export indicators of compromise associated with malware. IOCs can be exported in various formats such as MISP events, Suricata IDS Ruleset, Domain Host files, DNS Response Policy Zone, JSON files and CSV files.
Questions
The IOC 212.192.246.30:5555 is identified under which malware alias name on ThreatFox?
Answer
katana
Which malware is associated with the JA3 Fingerprint 51c64c77e60f3980eea90869b68c58a8 on SSL Blacklist?
Answer
dridex
From the statistics page on URLHaus, what malware-hosting network has the ASN number AS14061?
Answer
DIGITALOCEAN-ASN
Which country is the botnet IP address 178.134.47.166 associated with according to FeodoTracker?
Answer
Georgia
Task 5: PhishTool
Email phishing is one of the main precursors of any cyber attack. Unsuspecting users get duped into opening and accessing malicious files and links sent to them by email, as they appear to be legitimate. As a result, adversaries infect their victims’ systems with malware, harvesting their credentials and personal data and performing other actions such as financial fraud or conducting ransomware attacks.
For more information and content on phishing, check out these rooms:
Questions
Scenario: You are a SOC Analyst and have been tasked to analyse a suspicious email, Email1.eml. To solve the task, open the email using Thunderbird on the attached VM, analyse it and answer the questions below.
What social media platform is the attacker trying to pose as in the email?
Answer
What is the senders email address?
Answer
What is the recipient’s email address?
Answer
What is the Originating IP address? Defang the IP address.
Answer
204[.]93[.]183[.]11
How many hops did the email go through to get to the recipient?
Answer
4
Task 6: Cisco Talos Intelligence
IT and Cybersecurity companies collect massive amounts of information that could be used for threat analysis and intelligence. Being one of those companies, Cisco assembled a large team of security practitioners called Cisco Talos to provide actionable intelligence, visibility on indicators, and protection against emerging threats through data collected from their products. The solution is accessible as Talos Intelligence.
Cisco Talos encompasses six key teams:
- Threat Intelligence & Interdiction: Quick correlation and tracking of threats provide a means to turn simple IOCs into context-rich intel.
- Detection Research: Vulnerability and malware analysis is performed to create rules and content for threat detection.
- Engineering & Development: Provides the maintenance support for the inspection engines and keeps them up-to-date to identify and triage emerging threats.
- Vulnerability Research & Discovery: Working with service and software vendors to develop repeatable means of identifying and reporting security vulnerabilities.
- Communities: Maintains the image of the team and the open-source solutions.
- Global Outreach: Disseminates intelligence to customers and the security community through publications.
More information about Cisco Talos can be found on their White Paper
Questions
Task: Use the information gathered from inspecting the Email1.eml file from Task 5 to answer the following questions using Cisco Talos Intelligence. Please note that the VM launched in Task 5 would not have access to the Internet.
What is the listed domain of the IP address from the previous task?
Answer
scnet.net
What is the customer name of the IP address?
Answer
Complete Web Reviews
Scenario 1
Scenario: You are a SOC Analyst. Several suspicious emails have been forwarded to you from other coworkers. You must obtain details from each email to triage the incidents reported.
Task: Use the tools and knowledge discussed throughout this room (or use your resources) to help you analyze Email2.eml found on the VM attached to Task 5 and use the information to answer the questions.
Questions
According to Email2.eml, what is the recipient’s email address?
Answer
From Talos Intelligence, the attached file can also be identified by the Detection Alias that starts with an H…
Answer
HIDDENEXT/Worm.Gen
Scenario 2
Scenario: You are a SOC Analyst. Several suspicious emails have been forwarded to you from other coworkers. You must obtain details from each email to triage the incidents reported.
Task: Use the tools and knowledge discussed throughout this room (or use your resources) to help you analyze Email3.eml found on the VM attached to Task 5 and use the information to answer the questions.
Questions
What is the name of the attachment on Email3.eml?
Answer
Sales_Receipt 5606.xls
What malware family is associated with the attachment on Email3.eml?
Answer
Dridex