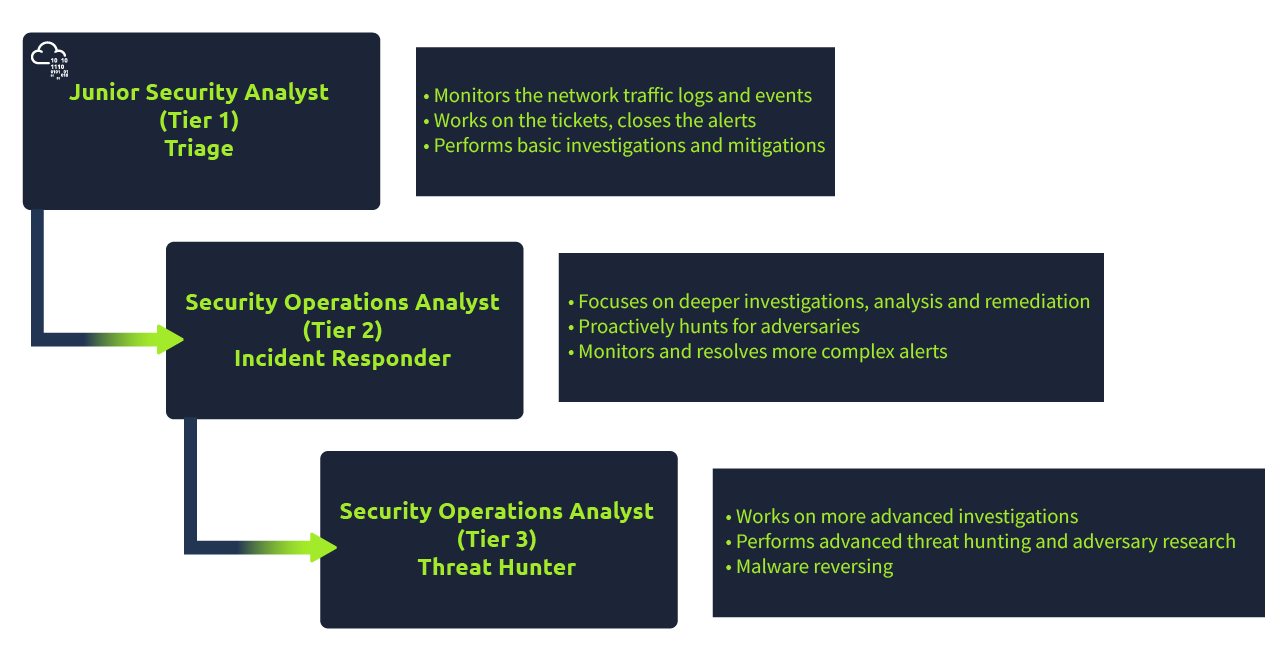
Task 1: A career as a Junior (Associate) Security Analyst
Question: What will be your role as a Junior Security Analyst?
Answer: Triage Specialist
In the Junior Security Analyst role, you will be a Triage Specialist. You will spend a lot of time triaging or monitoring the event logs and alerts.
The responsibilities for a Junior Security Analyst or Tier 1 SOC Analyst include:
- Monitor and investigate the alerts (most of the time, it’s a 24x7 SOC operations environment)
- Configure and manage the security tools
- Develop and implement basic IDS (Intrusion Detection System) signatures
- Participate in SOC working groups, meetings
- Create tickets and escalate the security incidents to the Tier 2 and Team Lead if needed
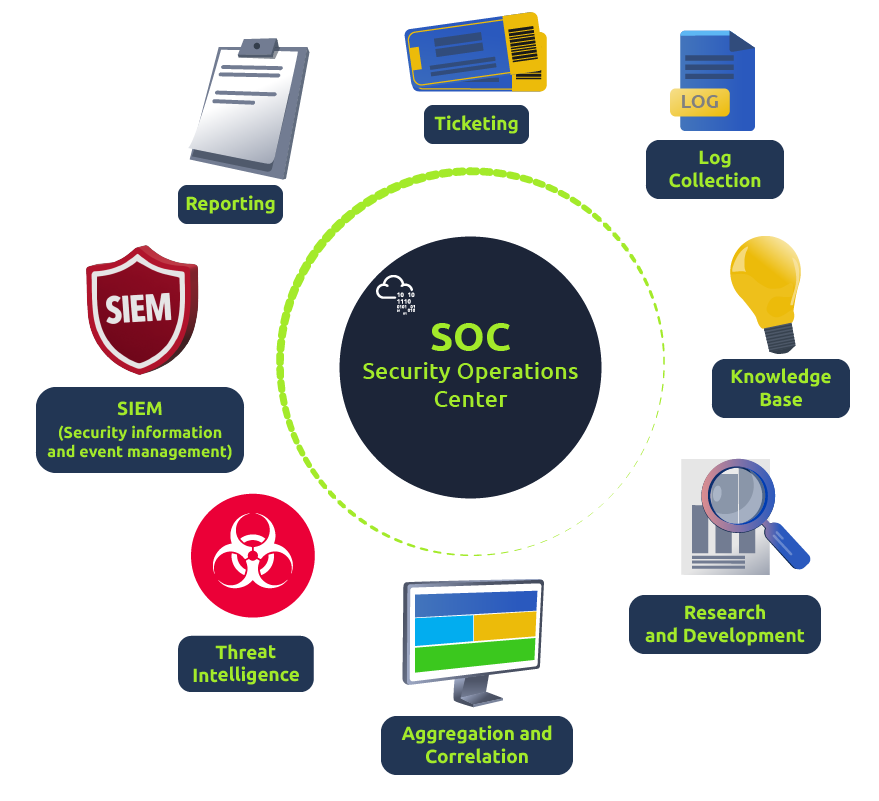
Task 2: Security Operations Center (SOC)
The core function of a SOC (Security Operations Center) is to investigate, monitor, prevent, and respond to threats in the cyber realm 24/7 or around the clock.
Preparation and Prevention
- Stay informed of the current cyber security threats (Twitter and Feedly can be great resources to keep up with the news related to Cybersecurity)
- Work on a security roadmap to protect the organisation, and be ready for the worst-case scenario.
- Prevention methods include gathering intelligence data on the latest threats, threat actors, and their TTPs (Tactics, Techniques, and Procedures).
- It also includes the maintenance procedures like updating the firewall signatures, patching the vulnerabilities in the existing systems, block-listing and safe-listing applications, email addresses, and IPs.
Monitoring and Investigation
- A SOC team proactively uses SIEM (Security information and event management) and EDR (Endpoint Detection and Response) tools to monitor suspicious and malicious network activities.
- As a Security Analyst, you will learn how to prioritise the alerts based on their level: Low, Medium, High, and Critical. Of course, it is an easy guess that you will need to start from the highest level (Critical) and work towards the bottom - Low-level alert.
- Having properly configured security monitoring tools in place will give you the best chance to mitigate the threat.
Response
After the investigation, the SOC team coordinates and takes action on the compromised hosts, which involves isolating the hosts from the network, terminating the malicious processes, deleting files, and more.
Task 3: A day In the life of a Junior (Associate) Security Analyst
Warning
Note that I don’t actually know if the IP is randomized across players, so you should probably
What was the malicious IP address in the alerts?
Answer:
221.181.185.159
To whom did you escalate the event associated with the malicious IP address?
Answer: Will Griffin
After blocking the malicious IP address on the firewall, what message did the malicious actor leave for you?
Answer:
THM{UNTIL-WE-MEET-AGAIN}